Pixel Perfect Ploy
Masking Executables as Image Files

Hiding exe with Image extension
What we always see is not what it is- A file could look innocent but it could hide the most dangerous malware. Windows hides file extensions by default, therefore there is an infinite possible ways to send a malware unnoticed, two way of doing it is hiding/attaching it with an image-
This blog is only for educational purpose and in no way intended for malicious purpose.
Method 1
We can start by playing with victims mind by sending some inappropriate/attractive picture which will attract them and open the file. So the first step is to find a picture, I will use this
Once we have done it, we will open a new .txt document-
We will then rename it to filename.ps1(.ps1 is a powershell extension) -
The next step is to edit the file, for me is the “seeyou.ps1”. Code given below:
After saving the code, we will use a software to merge the executable and image but before that we have to get an ico-file of the image.
Finally it should look like this-
Download the software from here- github and run it
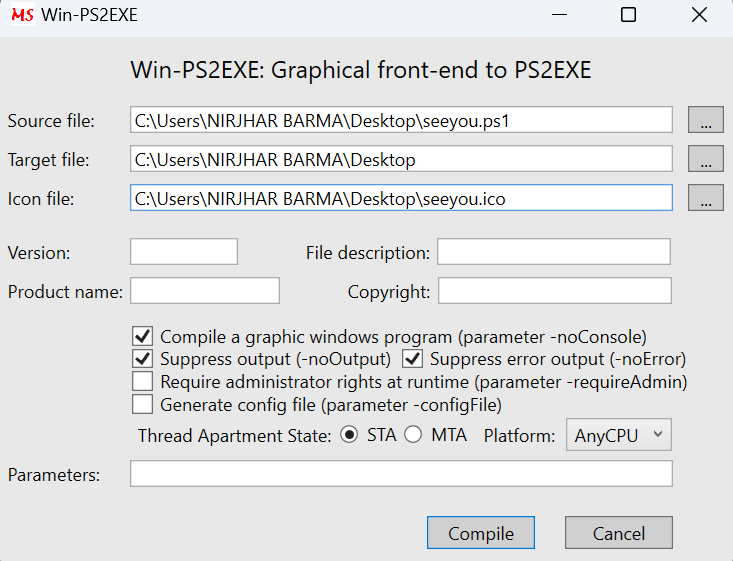
In the source file paste the .ps1 file path along with file name, in the icon file paste the .ico file path along with file name and tick/check the suppress output and suppress error output to hide any message. Once followed, press the compile button which will give another file.
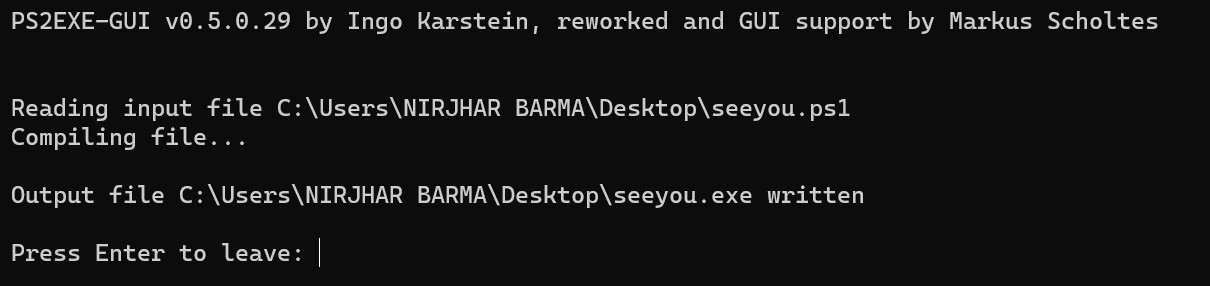
A file is created-
Now we will rename the file to “seeyou.jpg.exe” since windows extensions are turned off by default it will be impossible to notice unless the user has enabled it, generally people won’t notice but if you hover above the picture you will find the file version(pic representation given above).
Now there are some things to notice, firstly we need to obfuscate the powershell code so that it can bypass anti-virus, we can add some more advanced tech like heap spraying or shellcode injection or persistant backdoor, since this is just a walkthrough on how to craft such file we will not be exploring the advance parts.
Method 2
We will kick things off with a malware/trojan/logger and picture, don’t have a malware? Get it from vx-underground
Now we will bind the .exe and image file together into one using winRAR sfx archive option-.
Firstly we will select both the .exe and image file and select add to winRAR archive,
Then select create sfx archive.
Then move to advanced tab and click on SFX options, then click on setup tab and write the image file and .exe file name there
Then go to Modes tab and select unpack to temporary folder and hide all option
Then move to update tab, check the extract and update files and overwrite all files-
Finally go to Text and icon tab, select the .ico file of the image and upload there. Once completed, you can click on ok and close the window.
Aaand we have created a file but it has the file extension .exe, by default windows hides all file extensions but we don’t want to take any risks therefore we will use a very uncommon method known as Unitrix method. We will use the .scr(screen saver) extension to not make it suspicious, so it becomes peppa.jpg.scr now we will use the unitrix exploit, what it will do is override the words from right to left, which will be very hard to notice.
So we will choose to rename and write peppagpj.scr and put the cursor between peppa|gpj.scr and right click which will open a dialog box and choose Insert Unicode control character and then choose RLO(Right to Left Override)
The result will look like this when compared with the first output-
Yaay we have now successfully created an image embedded with a malware/trojan/spyware and disguised it.
How to prevent it
Like that we have learned how to craft an image with an embedded exe. But how to keep ourselves safe from such attacks? Firstly we have to be very cautious of what we download and open, we should enable some folder features which could come handy-
Or we can select the file and do alt+enter key to view its properties and determine what it is. When unsure of its contents use a sandbox.
Author: Nirjhar
